
Hello netter, apa kabar semua, kali ini saya akan membagikan animasi buatan saya dengan menggunakan flash 8 ( maaf hanya program ini yang saya punya ).
Masih cupu banget ...
You'll find something diffrent in this blog
| Nama Object | Event | Action |
| Obj_Bola • Spr_bola • Visible |
Step | • Comment : cek jika ada di udara • Check empty : x=0,y=1,only solid,relative di contreng • Set grafity : direction = 270, grafity = 0.5 • Else • Set grafity : direction = 270, grafity = 0 • Comment : batasi kecepatan vertical • Test variable : variable=vspeed,value=12,operation=Larger than • Speed vertical : vert.speed=12 |
| Collision Obj_Block |
• Move to cantact : direction=direction,maximum=12,against=solid object • Speed vertical : vert.speed=0 |
|
| Keyboard Left |
• Check empty : x=-4,y=0,only solid,relative di contreng • Jump to position : x=-4,y=0, relative di contreng |
|
| Keyboard Up |
• Chec collisionx=0,y=1,only solid,relative di contreng • Speed vertical vert.speed=-10 |
|
| Keyboard Right |
• Check empty x=4,y=0,only solid,relative di contreng • Jump to position x=4,y=0, relative di contreng |
|
| ini yang ke 7 |


| Nama Object | Event | Action |
|---|---|---|
| Obj_Tower_Boom; Spr_tower_boom | Step | Task chance : side = 10 ▲ <---- block="block" br="br" open="open"> Create moving Object : spr_boom,x=0,y=0,speed=8,direction=random_range(250,290),relative=dicontreng. ▼<---- block="block" br="br" close="close"> |
| Obj_boom Spr_boom |
Create | Move toward : x=player.x,y=player.y,speed=8 |

| Nama Object | Event | Action |
|---|---|---|
| Obj_score | Draw | • Set Color = ( pilih warna yang sesuai dengan anda) • Set Font : font ( klik font yang kita sudah buat), align = (left,center,right pilih salah satu) • Draw score: x=0,y=0,caption=”Score :”, Relative = dicontreng |

| Nama Object | Event | Action |
|---|---|---|
| Obj_score | Draw | 1.Draw score: x=43,y=43 ( x dan y adalah letak posisi tulisan score yang kita buat), caption = "Player 1" |
| 2.Draw lives:x=435,y=43,caption="Player 2" |

 Now continued to choose setting button right of interface of av. and now will show a popup windows like in sc.
Now continued to choose setting button right of interface of av. and now will show a popup windows like in sc.
 As you see in sc, I choose add button to put my keygen or my crack so the av can recognize that program not dangers and he gave me allow permission. After that I finish my work with choose ok button.
That all and I can usedmy keygen or crack for my programs. As ussually this educational purpose only do with your own risk see yeaaa .... :p
Note:
- sorry I found your bugs
As you see in sc, I choose add button to put my keygen or my crack so the av can recognize that program not dangers and he gave me allow permission. After that I finish my work with choose ok button.
That all and I can usedmy keygen or crack for my programs. As ussually this educational purpose only do with your own risk see yeaaa .... :p
Note:
- sorry I found your bugs



INTRO(3) Cygwin INTRO(3)
NAME
intro - Introduction to the Cygwin API
DESCRIPTION
Cygwin is a UNIX environment, developed by Red Hat, for Windows. It
consists of two parts:
A DLL (cygwin1.dll) which acts as a UNIX emulation layer providing
substantial UNIX API functionality. This page describes the API pro-
vided by the DLL.
A collection of tools, ported from UNIX, which provide UNIX/Linux look
and feel. This environment is described in the intro(1) man page.
AVAILABILITY
Cygwin is developed by volunteers collaborating over the Internet. It
is distributed through the website http://cygwin.com. The website has
extensive documentation, including FAQ, User's Guide, and API Refer-
ence. It should be considered the authoritative source of information.
The source code, relased under the GNU General Public License, Version
2, is also availalbe from the website or one of the mirrors.
COMPATIBILITY
Cygwin policy is to attempt to adhere to POSIX/SUSv2 (Portable Operat-
ing System Interface for UNIX / The Single UNIX Specification, Version
2) where possible.
SUSv2 is available online at:
http://www.opengroup.org/onlinepubs/007908799/
For compatibility information about specific functions, see the API
Reference at:
http://cygwin.com/cygwin-api/cygwin-api.html
Where these standards are ambiguous, Cygwin tries to mimic Linux.
However, Cygwin uses newlib instead of glibc as its C Library, avail-
able at:
http://sources.redhat.com/newlib/
Keep in mind that there are many underlying differences between UNIX
and Win32 (for example, a case-insensitive file system), making com-
plete compatibility an ongoing challenge.
REPORTING BUGS
If you find a bug in Cygwin, please read
http://cygwin.com/bugs.html
and follow the instructions for reporting found there. If you are
able to track down the source of the bug and can provide a fix, there
are instructions for contributing patches at:
http://cygwin.com/contrib.html
COPYRIGHT
Cygwin is Copyright (C) 1995, 1996, 1997, 1998, 1999, 2000, 2001,
2002, 2003, 2004, 2005 Red Hat, Inc.
Cygwin is Free software; for complete licensing information, refer to:
http://cygwin.com/licensing.html
MAINTAINER
This man page was written and is maintained by Joshua Daniel Franklin
REPORTING BUGS
If you find a bug in Cygwin, please read
http://cygwin.com/bugs.html
and follow the instructions for reporting found there. If you are
able to track down the source of the bug and can provide a fix, there
are instructions for contributing patches at:
http://cygwin.com/contrib.html
COPYRIGHT
Cygwin is Copyright (C) 1995, 1996, 1997, 1998, 1999, 2000, 2001,
2002, 2003, 2004, 2005 Red Hat, Inc.
Cygwin is Free software; for complete licensing information, refer to:
http://cygwin.com/licensing.html
MAINTAINER
This man page was written and is maintained by Joshua Daniel Franklin
server@lpia-server ~
$ whoami
server

FreeMem=(1280000000)
FreeMem=(2560000000)
FreeMem=(5120000000)
FreeMem=(10240000000)
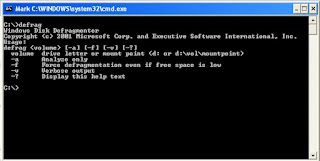
C:\>jhead_2.exe -h
Jhead is a program for manipulating settings and thumbnails in Exif jpeg header
used by most Digital Cameras. v2.95 Matthias Wandel, Mar 16 2012.
http://www.sentex.net/~mwandel/jhead
Usage: jhead_2.exe [options] files
Where:
files path/filenames with or without wildcards
[options] are:
GENERAL METADATA:
-te Transfer exif header from another image file
Uses same name mangling as '-st' option
-dc Delete comment field (as left by progs like Photoshop & Compupic)
-de Strip Exif section (smaller JPEG file, but lose digicam info)
-di Delete IPTC section (from Photoshop, or Picasa)
-dx Deletex XMP section
-du Delete non image sections except for Exif and comment sections
-purejpg Strip all unnecessary data from jpeg (combines -dc -de and -du)
-mkexif Create new minimal exif section (overwrites pre-existing exif)
-ce Edit comment field. Uses environment variable 'editor' to
determine which editor to use. If editor not set, uses VI
under Unix and notepad with windows
-cs Save comment section to a file
-ci Insert comment section from a file. -cs and -ci use same naming
scheme as used by the -st option
-cl string Insert literal comment string
DATE / TIME MANIPULATION:
-ft Set file modification time to Exif time
-dsft Set Exif time to file modification time
-n[format-string]
Rename files according to date. Uses exif date if present, file
date otherwise. If the optional format-string is not supplied,
the format is mmdd-hhmmss. If a format-string is given, it is
is passed to the 'strftime' function for formatting
In addition to strftime format codes:
'%f' as part of the string will include the original file name
'%i' will include a sequence number, starting from 1. You can
You can specify '%03i' for example to get leading zeros.
This feature is useful for ordering files from multiple digicams t
sequence of taking. Only renames files whose names are mostly
numerical (as assigned by digicam)
The '.jpg' is automatically added to the end of the name. If the
destination name already exists, a letter or digit is added to
the end of the name to make it unique.
The new name may include a path as part of the name. If this path
does not exist, it will be created
-a (Windows only) Rename files with same name but different extension
Use together with -n to rename .AVI files from exif in .THM files
for example
-ta<+|->h[:mm[:ss]]
Adjust time by h:mm backwards or forwards. Useful when having
taken pictures with the wrong time set on the camera, such as when
traveling across time zones or DST changes. Dates can be adjusted
by offsetting by 24 hours or more. For large date adjustments,
use the -da option
-da-
Adjust date by large amounts. This is used to fix photos from
cameras where the date got set back to the default camera date
by accident or battery removal.
To deal with different months and years having different numbers o
days, a simple date-month-year offset would result in unexpected
results. Instead, the difference is specified as desired date
minus original date. Date is specified as yyyy:mm:dd or as date
and time in the format yyyy:mm:dd/hh:mm:ss
-ts
C:\>jhead_2.exe -purejpg galau.jpg
Modified: galau.jpg
C:\>jhead_2.exe -ce galau.jpg
C:\>jhead_2.exe galau.jpg
File name : galau.jpg
File size : 27712 bytes
File date : 2012:05:29 11:24:19
Resolution : 506 x 337
Comment : Abina azkia
Comment : was
Comment : here

http://www.4shared.com/mp3/t956GQQt/Last_Child_-_Lagu_terakhir_unt.htm <-- url download 4shared.com
http://www.4server.info/download/http://www.4shared.com/mp3/t956GQQt/Last_Child_-_Lagu_terakhir_unt.htm <--- setelah di generate


The message reads:
Confirm your e-mail account please enter your Mailbox Details by clicking the link below:
[LINK]
Failure to provide details correctly will result to immediate closure of your mailbox account from our database.

The email reads as follows:
Subject: MAIL QUOTA 89.99%(VALIDATE)
Helpdesk requires you to validate your webmail.
Due to our upgrade, Protecting your webmail account is our primary concern, revalidate your e-mail by clicking [LINK] help desk.



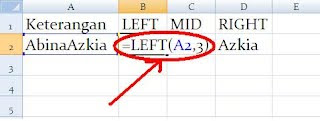
=LEFT(A2,3)
- A2 adalah sebagai cell acuan.
- 3 adalah jumlah atau banyaknya karakter di kiri yang dibutuhkan.
maka hasilnya menjadi "Abi"

=RIGHT(A2,5)
- A2 adalah sebagai cell acuan.
- 5 adalah jumlah atau banyaknya karakter di kanan yang dibutuhkan.
maka hasilnya menjadi "Azkia"
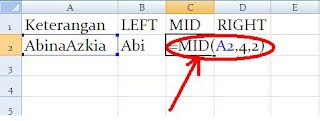
=MID(A2,4,2)
- A2 adalah sebagai cell acuan.
- 4 adalah urutan karakter cell acuan yang dihitung dari kiri ke arah kanan
-
- 2 adalah jumlah atau banyaknya karakter ditengah yang dibutuhkan.
maka hasilnya menjadi "na"

LEFT --> =IF(LEFT(CELL ACUAN,JML KARAKTER)=LOGIKA TEST,EXPhttp://www.blogger.com/img/blank.gif1,EXP2) <-- DUA TINGKAT IF
RIGHT --> =IF(RIGHT(CELL ACUAN,JML KARAKTER)=LOGIKA TEST,EXP1,EXP2)<-- DUA TINGKAT IF
MID --> =IF(MID(CELL ACUAN,URUTAN KARAKTER,JML KARAKTER)=LOGIKA TEST,EXP1,EXP2)<-- DUA TINGKAT IF



C:\>tasklist
Image Name PID Session Name Session# Mem Usage
========================= ====== ================ ======== ============
System Idle Process 0 Console 0 16 K
System 4 Console 0 36 K
smss.exe 556 Console 0 44 K
csrss.exe 612 Console 0 1,752 K
winlogon.exe 640 Console 0 4,584 K
services.exe 684 Console 0 1,692 K
lsass.exe 696 Console 0 1,340 K
svchost.exe 848 Console 0 1,524 K
svchost.exe 904 Console 0 1,304 K
svchost.exe 968 Console 0 11,916 K
aips.exe 1004 Console 0 296 K
svchost.exe 1132 Console 0 1,236 K
svchost.exe 1196 Console 0 2,976 K
explorer.exe 1368 Console 0 15,612 K
spoolsv.exe 1456 Console 0 5,820 K
igfxtray.exe 1604 Console 0 280 K
hkcmd.exe 1612 Console 0 300 K
igfxpers.exe 1620 Console 0 268 K
jusched.exe 1632 Console 0 36 K
egui.exe 1644 Console 0 3,864 K
daemon.exe 1652 Console 0 296 K
ctfmon.exe 1736 Console 0 728 K
ToolwizCares.exe 1780 Console 0 3,028 K
IDMan.exe 1820 Console 0 1,392 K
USB Disk Security.exe 1972 Console 0 2,000 K
AdskScSrv.exe 2008 Console 0 256 K
mscorsvw.exe 2032 Console 0 1,196 K
ekrn.exe 260 Console 0 31,976 K
E_S40ST7.EXE 264 Console 0 36 K
E_S40RP7.EXE 300 Console 0 44 K
jqs.exe 328 Console 0 1,392 K
raysat_3dsmax9_32server.e 512 Console 0 40 K
NHOSTSVC.EXE 524 Console 0 32 K
PsiService_2.exe 188 Console 0 40 K
svchost.exe 824 Console 0 36 K
netcut.exe 1320 Console 0 6,388 K
IEMonitor.exe 2568 Console 0 396 K
svchost.exe 2628 Console 0 176 K
Adobe Photoshop CS3.exe 2352 Console 0 212 K
Photoshop.exe 796 Console 0 12,052 K
firefox.exe 2456 Console 0 238,224 K
plugin-container.exe 2140 Console 0 82,812 K
DnsJumper.exe 3300 Console 0 1,364 K
cmd.exe 4036 Console 0 804 K
tasklist.exe 3324 Console 0 4,144 K
wmiprvse.exe 740 Console 0 5,308 K
C:\>tasklist >> Im_here.txt
C:\>dir
Volume in drive C has no label.
Volume Serial Number is D406-A40E
Directory of C:\
05/30/2012 11:24 AM 3,506 echo.txt
05/30/2012 11:29 AM 35 hore.txt
05/30/2012 11:53 AM 3,506 Im_here.txt <----- ini file nya
13 File(s) 16,468,981 bytes
8 Dir(s) 4,539,170,816 bytes free
 Facebook saat ini adalah sebuah jejaring social yang sangat terkenal dan banyak diminati orang sedunia. Karena banyak sekali ragam fitur nya, games dan lain2x. Tapi bukanlah hal yang baru dan sudah lumrah sebuah website mempunyai sebuah pertahanan yang cukup tangguh. Akan tetapi bukan berarti sekelas facebook tidak bisa di susupi, Karena kalo kita jeli sekarang ini banyak sekali para geek bertebaran di facebook, dan mereka mendirikan group dan bendera masing-masing.
Facebook saat ini adalah sebuah jejaring social yang sangat terkenal dan banyak diminati orang sedunia. Karena banyak sekali ragam fitur nya, games dan lain2x. Tapi bukanlah hal yang baru dan sudah lumrah sebuah website mempunyai sebuah pertahanan yang cukup tangguh. Akan tetapi bukan berarti sekelas facebook tidak bisa di susupi, Karena kalo kita jeli sekarang ini banyak sekali para geek bertebaran di facebook, dan mereka mendirikan group dan bendera masing-masing.
Common name Koobface
Aliases
OSX/Koobface.A (Intego)
W32/Koobfa-Gen (Sophos)
W32.Koobface.A (Symantec)
W32/Koobface.worm (McAfee)
WORM_KOOBFACE.DC (Trend Micro)
Win32/Koobface (CA, Inc.)
Worm.KoobFace (Malwarebytes)
Net-Worm.Win32.Koobface.a (Kaspersky)
Worm/Win32.Koobface (AhnLab)
Classification Unknown
Type Computer worm
Subtype Malware
Point of Origin Russia

 Hallo para netter sekalian ada yang pernah bilang pada saya,"kalo anda banyak mengetahui kata kunci atau keyword di google atau google dork, maka anda bisa dengan mudah melakukan hacking, exploitasi".
Hallo para netter sekalian ada yang pernah bilang pada saya,"kalo anda banyak mengetahui kata kunci atau keyword di google atau google dork, maka anda bisa dengan mudah melakukan hacking, exploitasi".
Latest Google Hacking Entries
Date Title Category
2012-01-10 inurl:wp-content/plugins/age-verification/age-veri... Advisories and Vulnerabilities
2012-01-03 inurl:"/showPlayer.php?id=" intext:"... Advisories and Vulnerabilities
2011-12-29 inurl:"mod.php?mod=blog" intext:"po... Advisories and Vulnerabilities
2011-12-28 inurl:cgi-bin/cosmobdf.cgi? Various Online Devices
2011-12-27 allintext:D.N.I filetype:xls Files containing juicy info
2011-12-27 (username=* | username:* |) | ( ((password=* | pas... Files containing passwords
2011-12-27 inurl:RgFirewallRL.asp | inurl:RgDmzHost.asp | inu... Various Online Devices
2011-12-26 intitle:SpectraIV-IP Various Online Devices
2011-12-26 "Powered by kryCMS" Advisories and Vulnerabilities
2011-12-23 inurl:.php intitle:- BOFF 1.0 intext:[ Sec. Info ] Vulnerable Servers






=IF(CELL ACUAN=LOGIKA TEST,EXPRESI 1,EXPRESI 2) <---- Jika IF dua tingkat

=IF( ---> Jika
F7 ---> NILAI RATA-RATA ---> Cell acuan
<60 ---> kurang dari atau sama dengan 60 ---> Logika test
, ---> maka (Note = , atau ; berdasarkan dari setting komputer/laptop yang kita gunakan.
"GAGAL" ---> Expresi 1
,"LULUS" ---> Expresi 2 atau Expresi terakhir
 Hallo para netter apakabar, kali ini saya coba posting mungkin bukan hal yang baru bagi anda, tapi bagi saya adalah sebagai hal yang baru, dan saya ingin anda juga bisa.
Hallo para netter apakabar, kali ini saya coba posting mungkin bukan hal yang baru bagi anda, tapi bagi saya adalah sebagai hal yang baru, dan saya ingin anda juga bisa. Design by Editor . Themes by Editor , Visco Foam Mattress & Editor .